Enterprise Security
MFA and More for Business
Passwordless Auth. Secure OTP.
Zero Trust.
Passwordless Authentication. Secure OTP. Zero Trust Security Model.
Is Your Organization Really Protected ?
Digital transformation has shifted into high gear with the increased usage of IoT, cloud computing, industry 4.0, blockchain and additional next generation technologies. In parallel, enterprise security needs to be a top priority as the frequency of security breaches and cyber-attacks grow.
Software-based security solutions are no longer good enough, and are specifically vulnerable to phishing attacks. Usernames and passwords are easy to hack and 2FA solutions are vulnerable to identity swap attacks. To protect accounts and secure access to valuable data and critical systems, organizations need to look elsewhere for solutions that authenticate employees or IoT devices.
A hardware-based, revocable public key infrastructure (PKI) solution adds robust security to prevent, among others, SIM swaps, identity theft and personal data leakage, during a wide range of activities including money transfers, social network MFA, SaaS access control, digital assets protection and more.
Is Your Organization Really Protected ?
Digital transformation has shifted into high gear with the increased usage of IoT, cloud computing, industry 4.0, blockchain and additional next generation technologies. In parallel, enterprise security needs to be a top priority as the frequency of security breaches and cyber-attacks grow.
Software-based security solutions are no longer good enough, and are specifically vulnerable to phishing attacks. Usernames and passwords are easy to hack and 2FA solutions are vulnerable to identity swap attacks. To protect accounts and secure access to valuable data and critical systems, organizations need to look elsewhere for solutions that authenticate employees or IoT devices.
A hardware-based, revocable public key infrastructure (PKI) solution adds robust security to prevent, among others, SIM swaps, identity theft and personal data leakage, during a wide range of activities including money transfers, social network MFA, SaaS access control, digital assets protection and more.
Revocable PKI Solution
Meet the first ever SIM-based hardware secure module (HSM). By leveraging the cellular signaling network and the cryptographic signatures on the SIM card, we have turned the SIM into a “cold wallet” that stores private keys to allow secure signatures. Now, businesses can boast secure wireless with a cellular-based authentication solution that includes cryptographic signatures and the capability to manage the PKI with either a decentralized or centralized policy management.
Proven Technology
Proven Technology
Secure OTP / Signature Request
One-time PINS (OTP) have limited utility for many businesses. OTP over SMS is unencrypted and code generators and authenticators are often difficult to use on mobile devices.
Instead, with Monogoto, developers can simply leverage the authentication interface with their organization’s backend adding superior security measures, replacing unsafe SMS delivery with a trusted signature process.
Do You Want to Learn About Our Enterprise
Security Solution?
Do You Want to Learn About Our Enterprise Security Solution(Contact us)
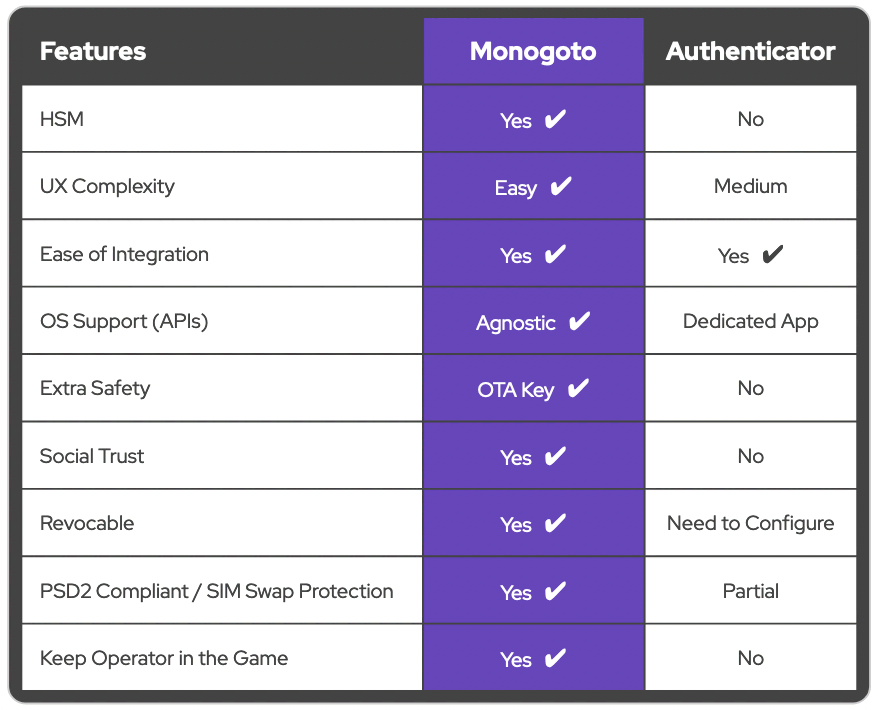
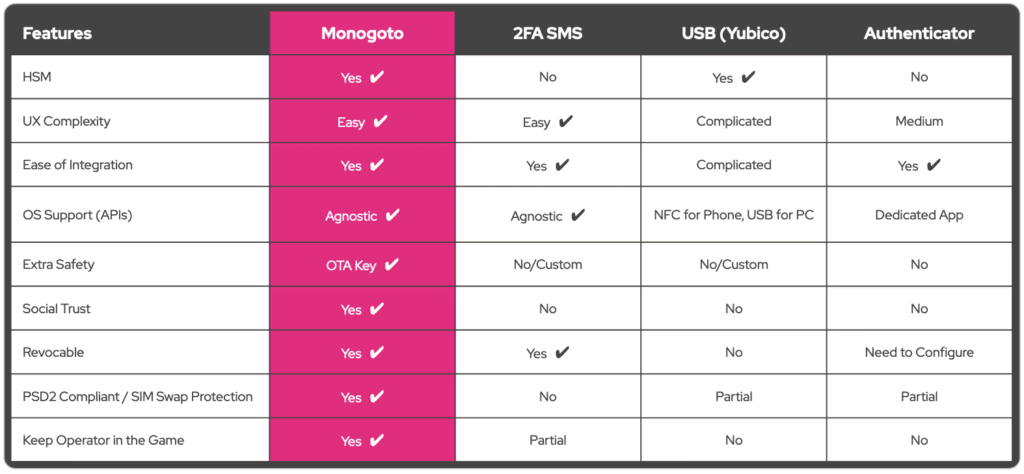
Why Monogoto ?
Superior than existing 2FA SMS.
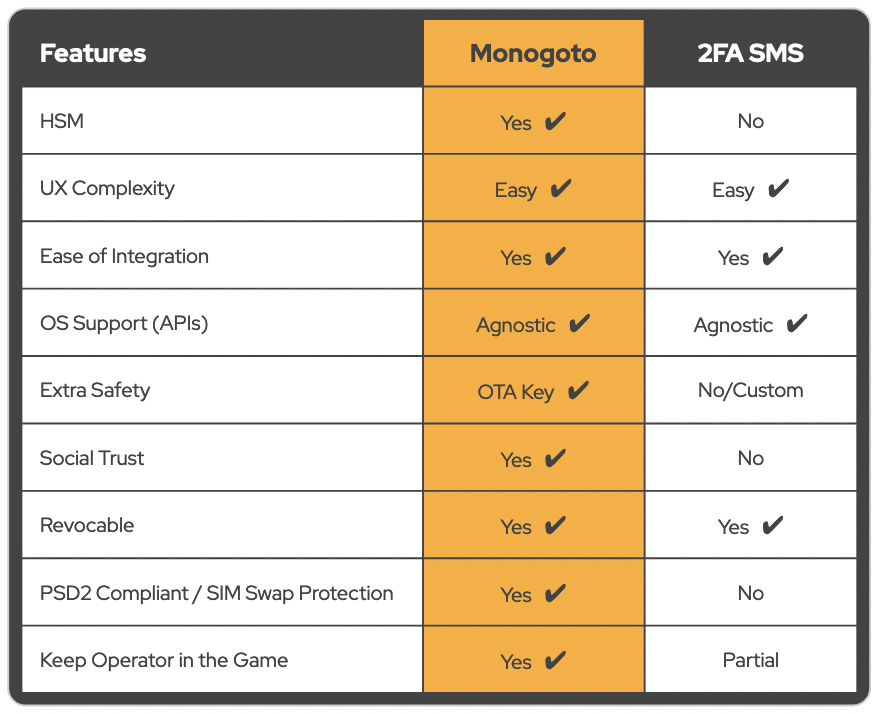
Build your own user experience.
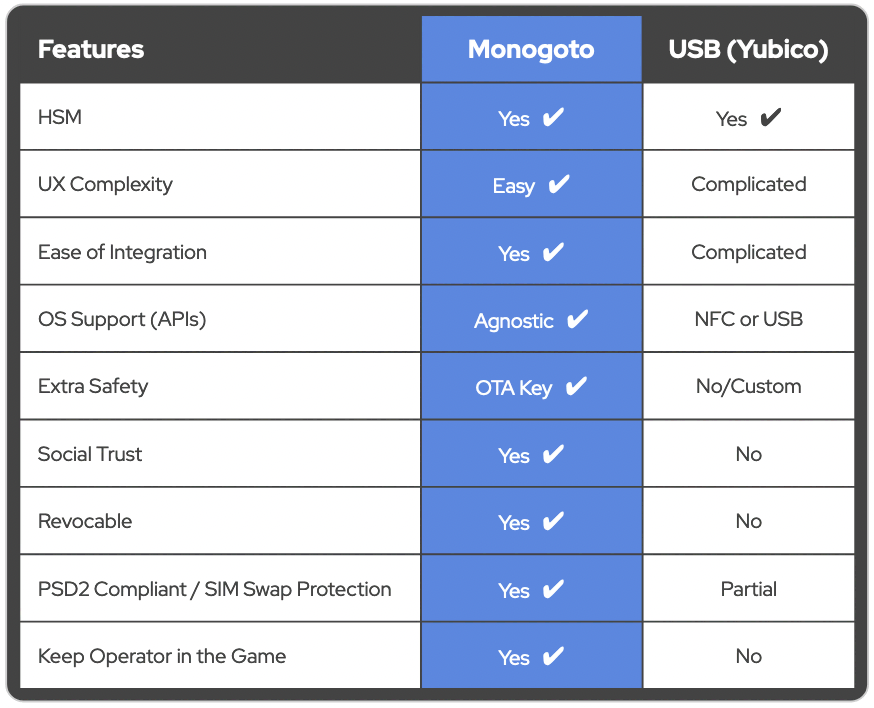
Keeping your private keys safe.